Welcome to PR TECH NEWS; check out ELK ItsyBitsy Solution here.
- Here I show you how to Put your ELK knowledge together and investigate an incident.

Turn on the machine and, start the attack box, wait for a few mins, Now in the attack box paste the machine IP in browser(Mozilla) and load the Elastic. If you get 502 error, wait for a minute and refresh the page.
2. Now in the Dashboard, set the required date, from 1st March 2022 to 31 March 2022
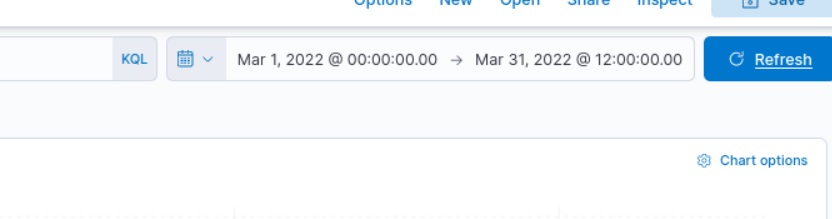
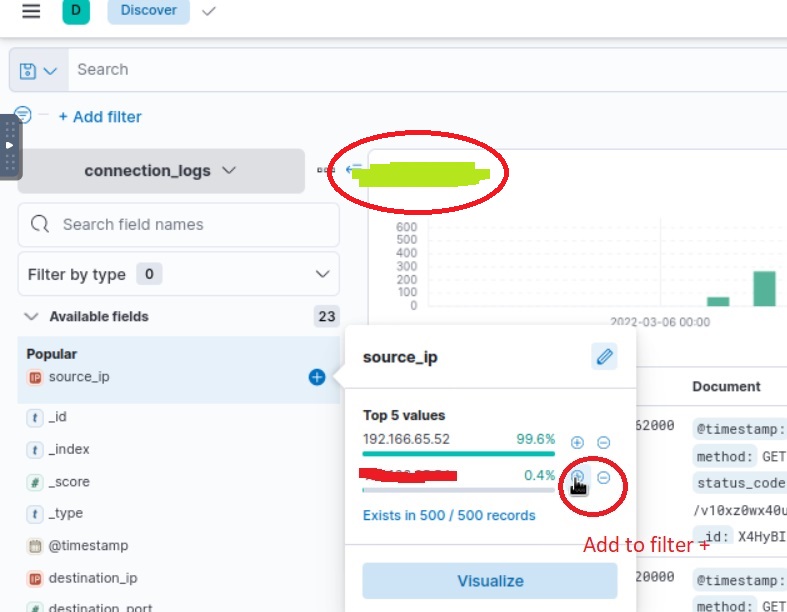
3. After the date now you can see the number of hits (answer 1) move to the Left Panel and select the IP address as shown below(answer 2), which has the least count(0.4%) but is malicious use + symbol and add it to filter to get further answers.
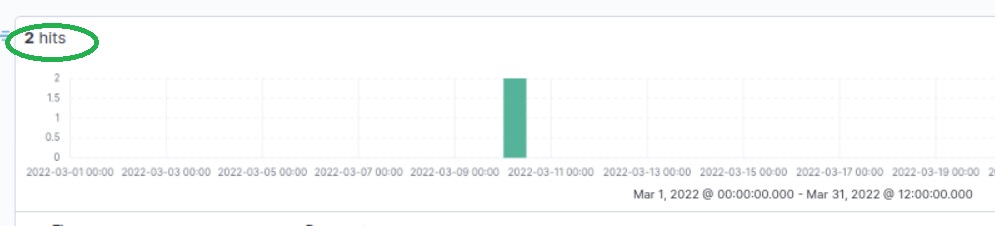
4. After Filtering new IP, you will be left with 2 Hits, as in the below figure and you are moving in the right way to get all answer
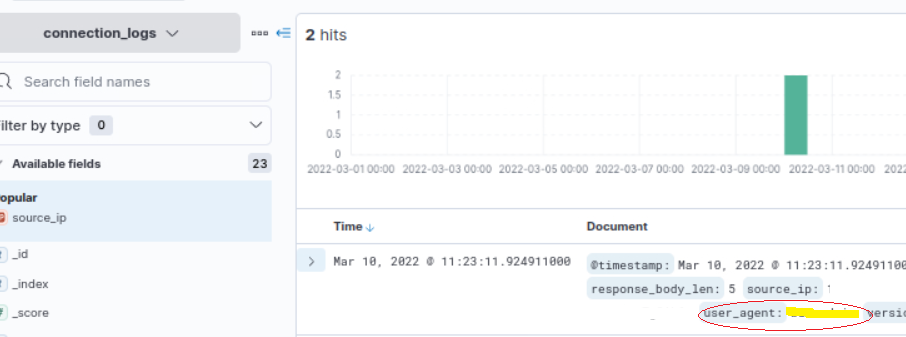
5. Now in the Logs (document) you can see the 2 incidents recorded, and the answer for binary(answer 3) will be the user agent as marked in yellow in below image.
6. Now from another field host you get the answer for (answer 4) What is the name of the filesharing site?
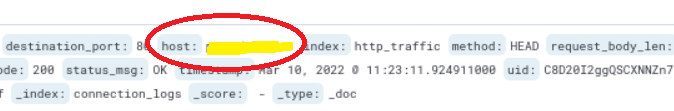
7. Next (answer -5) What is the full URL of the C2 to which the infected host is connected?
As you have already found the host above, to get the full URL you just need to find the URI field and combine it with the host. The field shown in the below image.
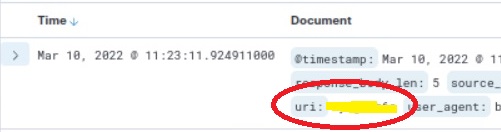
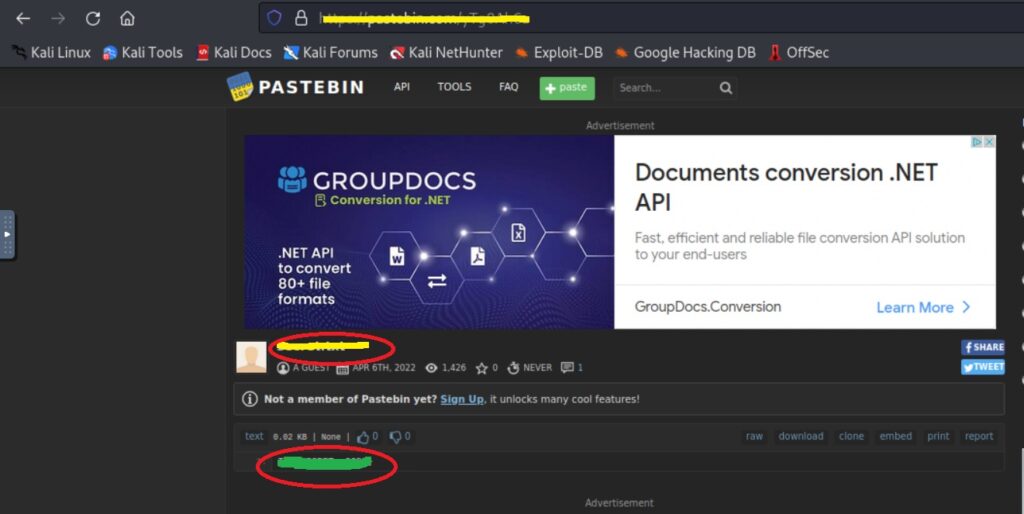
8. Now you have the Full URL use it in the attack box browser to get the file name(answer – 6) and scroll down to get the final flag (answer – 7), illustrated below.
Done ! – YOU HAVE CRACKED THE ROOM ItsyBitsy tryhackme !!!!!
Check out our other articles about LIFE, TECHNOLOGY & SPIRITUALITY !!
